Introduction
Extended Protection (EP) is a security feature incorporated into the Internet Information Services (IIS) on Windows Server. It’s designed to enhance the security of web communications by mitigating certain types of attacks, particularly those targeting the authentication process. This feature primarily focuses on safeguarding against man-in-the-middle (MITM) attacks and other related threats.
At its core, EP strengthens the authentication process between clients and servers by requiring additional verification steps. It ensures that both the client and server authenticate each other securely, thus minimizing the risk of impersonation or unauthorized access.
EP operates on a per-application basis within IIS and only applies to applications that have Windows authentication enabled. By introducing the concept of channel binding tokens, which bind each request to the specific channel used for communication, Extended Protection prevents attackers from intercepting and replaying authentication tokens in an attempt to gain unauthorized access to the server or hijack user sessions.
EP is available from Windows Server 2012 R2 to Windows Server 2022 and has been supported by Exchange 2016 and Exchange 2019 since August 2022.
By enabling EP in IIS, administrators can bolster the security posture of their web servers, providing an additional layer of defense against sophisticated attacks targeting the authentication process. It’s worth noting that while Extended Protection enhances security, it may also introduce some overhead due to the additional verification steps involved. However, the benefits of heightened security typically outweigh any minor performance impacts.
Enabling EP with Exchange 2016/2019 improves security and addresses significant security vulnerabilities. Activation should be done according to Microsoft’s recommendations. EP should not be activated on all Exchange applications present in IIS.
EP prerequisites with Exchange 2016/2019
It is highly recommended to strictly configure TLS 1.2/1.3 on Exchange 2016/2019 servers before enabling the EP feature and it is mandatory to have the same configuration across all servers that are members of a DAG cluster. Two types of configurations must be applied: One related to the support of encryption algorithms (disabling RC2/RC4/DES/3DES/MD5/SHA1/TLS1.0/TLS1.1 algorithms) and another related to the support of encryption algorithms in the .NET modules. The registry keys to apply are as follows.
Registry keys for the system (rebbot after apply this):
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
"AllowInsecureRenegoClients"=dword:00000000
"AllowInsecureRenegoServers"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\AES 128/128]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\AES 256/256]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\NULL]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 128/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 56/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\CipherSuites]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes\MD5]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes\SHA]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes\SHA256]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes\SHA384]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Hashes\SHA512]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman]
"Enabled"=dword:ffffffff
"ServerMinKeyBitLength"=dword:00000800
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\ECDH]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\PKCS]
"Enabled"=dword:ffffffff
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"Enabled"=dword:00000001
"DisabledByDefault"=dword:00000000
Registry keys for .NET modules (Powershell commands):
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWordFurthermore, it is necessary to configure the Outlook Anywhere service without the SSLOffloading option.
Set-OutlookAnywhere '<EXCHANGE_SERVER>\RPC (Default Web Site)' -SSLOffloading $false -InternalClientsRequireSsl $true -ExternalClientsRequireSsl $trueEP prerequisites with load-balancers and WAF
If you are using a load balancer that manages SSL termination (SSL-BRIDGING) to enhance the management of your public certificates, to utilize the WAF function, or to have an external connection name different from the internal connection name, you will need to adjust your configuration so that Exchange access with Windows authentication works with EP enabled. It is important to understand that EP will only affect services with Windows authentication. If you are only publishing Exchange webmail through a load balancer that manages SSL termination with form-based authentication, enabling EP will not impact your published service. Indeed, Microsoft Exchange only supports EP with a load balancer that handles SSL termination in only one case: SSL6BRIDGING with the same certificate installed on both the Exchange servers and the load balancer.
| Client usage | Certificate on the load-balancer is the same as the certificate used on Exchange servers with EP enabled | Connection status |
| POP3S/IMAP4S/SMTPS | NA | OK EP doesn’t impact POP/IMAP/SMTP protocols. |
| OWA with form authentification | NA | OK EP doesn’t impact WEB application without Windows authentication enabled. |
| OWA with Windows authentication / MAPI / RPC-HTTP / ACTIVESYNC / EWS | Yes | OK EP is supported in this case. |
| OWA with Windows authentication / MAPI / RPC-HTTP / ACTIVESYNC / EWS | No | KO Authentication failed during connection. |
| Autodiscover | NA | KO Microsoft doesn’t support EP on Autodiscover application |
EP configuration on Exchange 2016/2019 with Microsoft official script
Microsoft provides a PowerShell script (ExchangeExtendedProtectionManagement.ps1) that allows configuring EP on Exchange servers while staying within the matrix of Microsoft’s recommendations: Enabling EP on web services without enabling it on the Autodiscover service. The script checks TLS settings and then allows configuring/viewing the EP status on the various Exchange web services.
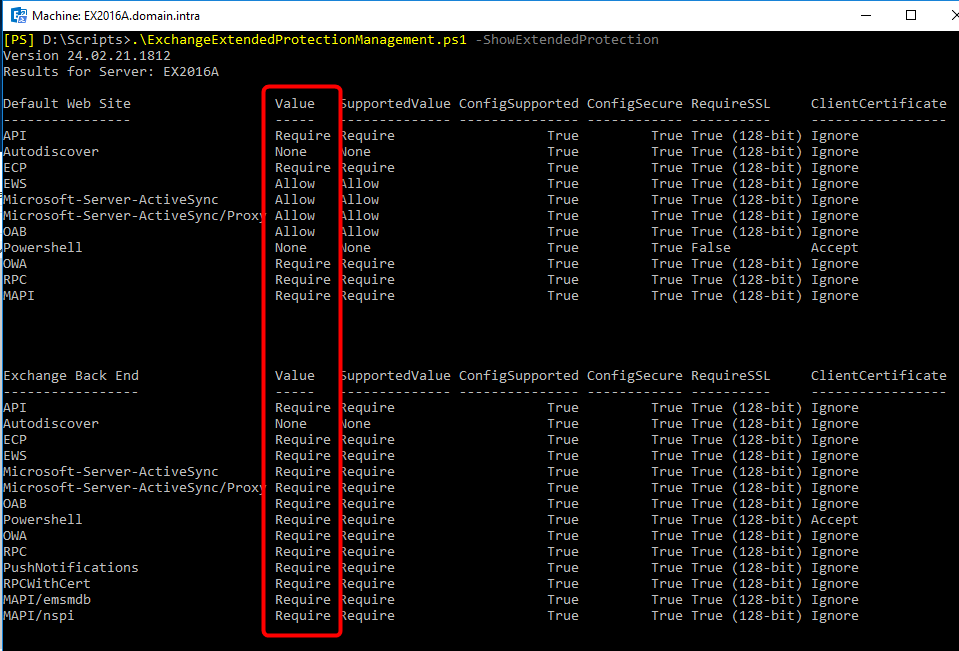
To view EP configuration the syntax is:
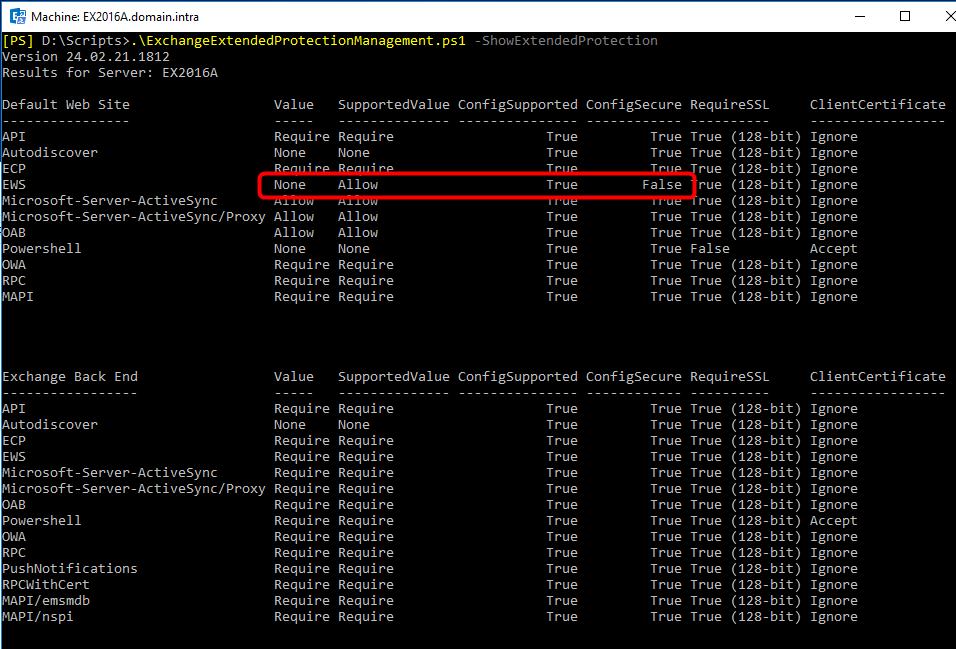
ExchangeExtendedProtectionManagement.ps1 -ShowExtendedProtection
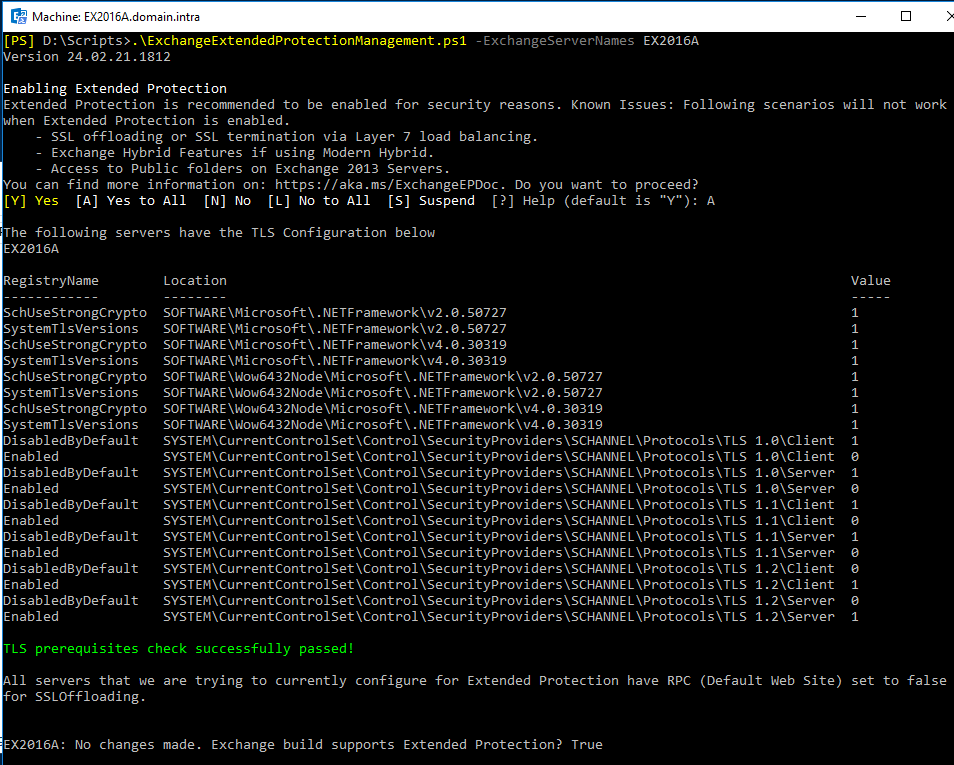
To enable EP on an Exchange server the syntax is:
ExchangeExtendedProtectionManagement.ps1 -ExchangeServerNames <SERVER>
To enable EP on multiple Exchange servers the syntaxes are:
ExchangeExtendedProtectionManagement.ps1 -ExchangeServerNames <SERVER1>,<SERVER2>
or
ExchangeExtendedProtectionManagement.ps1
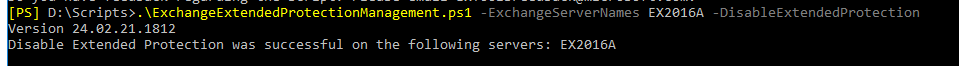
To disable EP on an Exchange server the syntax is:
ExchangeExtendedProtectionManagement.ps1 -DisableExtendedProtection
Note: It is possible to visually verify that EP is enabled on a web application. EP is an option of an application’s Windows authentication. Use the action “Advanced settings” menu of Windows Authentication feature to see EP status.
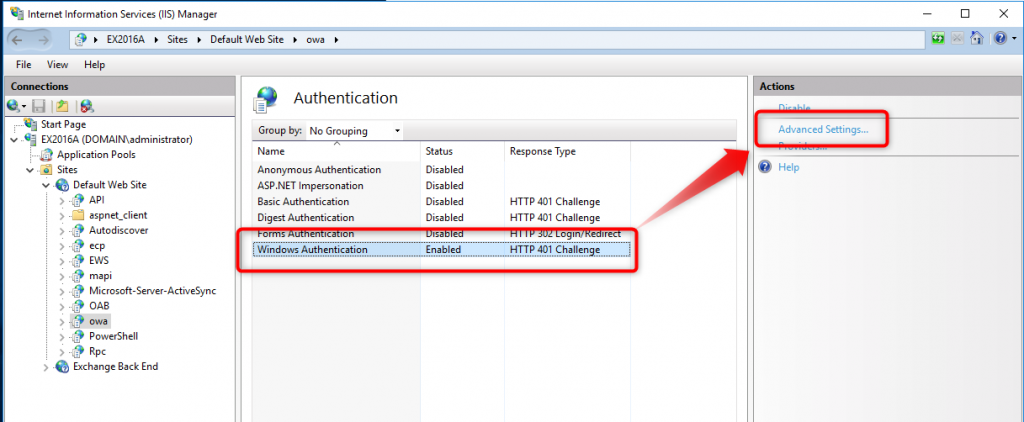
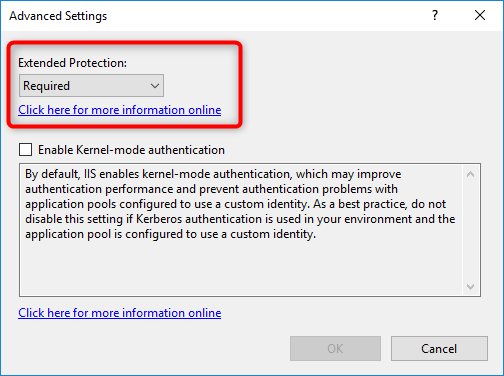
Note: EP with MS365 hybrid configuration
When your Exchange platform is hybridized with MS365, MS365 services need to access the EWS services on your internal servers and an EWS access point is published on the internet. This access point must necessarily provide an EWS endpoint with a public certificate, and it is possible that your internal platform uses private certificates. Since it is not possible to have private names (such as .intra) in a public certificate, it will not be possible to have an unique certificate in the EWS connection chain. With EP enabled on internal Exchange servers, the EWS connection from MS365 will not work, and hybrid configuration will be impacted. The only solution will be to change the internal architecture to use only public names with split DNS to differentiate internal and external access. This change is very heavy.
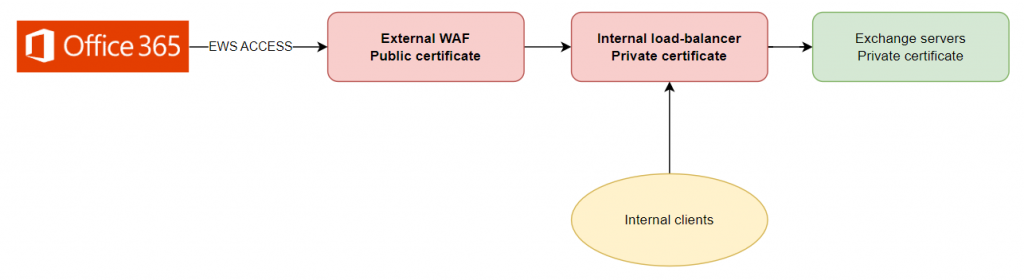
Microsoft has anticipated this scenario, and the -ExcludeVirtualDirectories EWSFrontEnd option of the PowerShell configuration script allows enabling EP on your Exchange servers without activating EP on the EWS service.
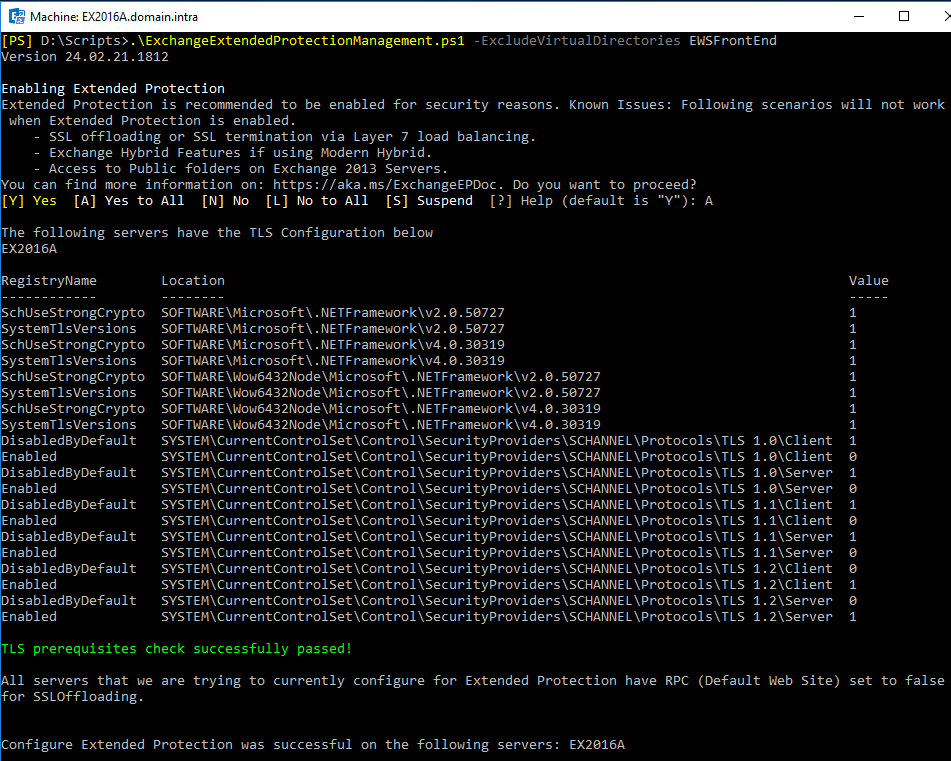
With this configuration, the Exchange hybrid configuration will not be impacted, but the EWS service will not be protected by EP, neither on the Internet nor on the internal network. This type of configuration is supported but not really secure.
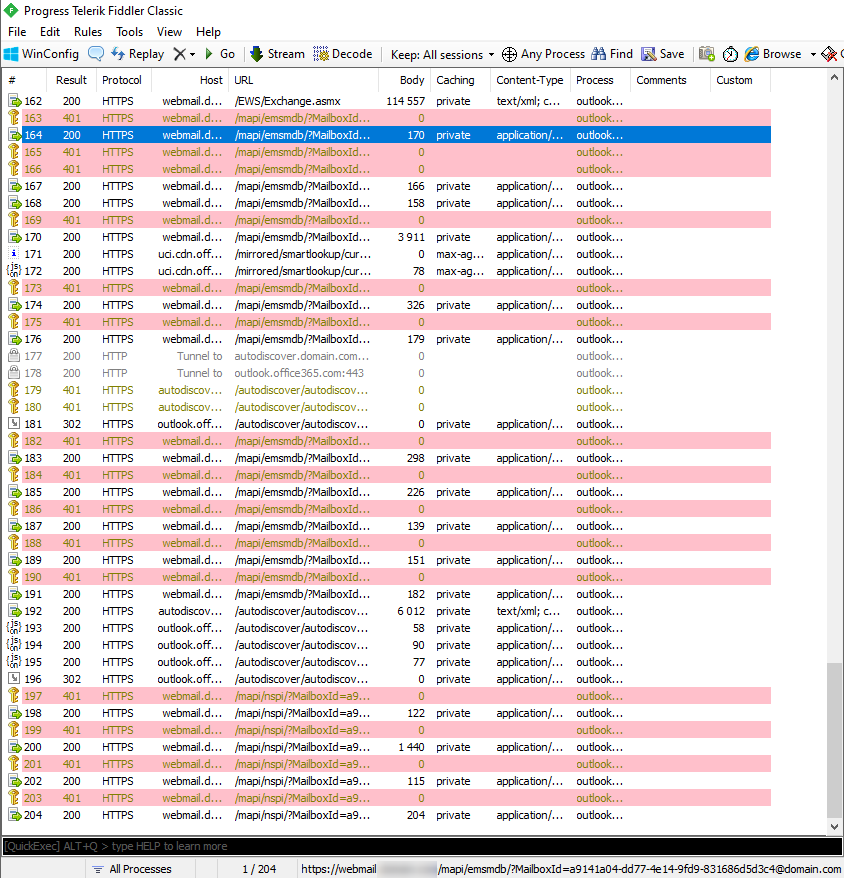
Note: Using Fiddler with EP enabled
If you want to use FIDDLER to debug an Exchange connection on a PC (with EP enabled), it will be impossible to connect.
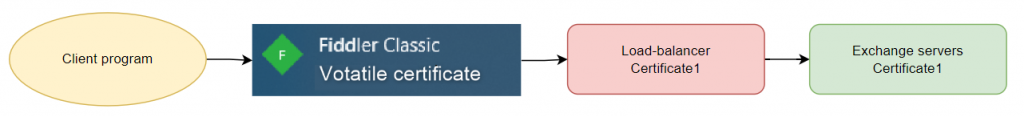
Indeed, FIDDLER will break the SSL connection chain by using a generated certificate in order to read the contents of the SSL packets.
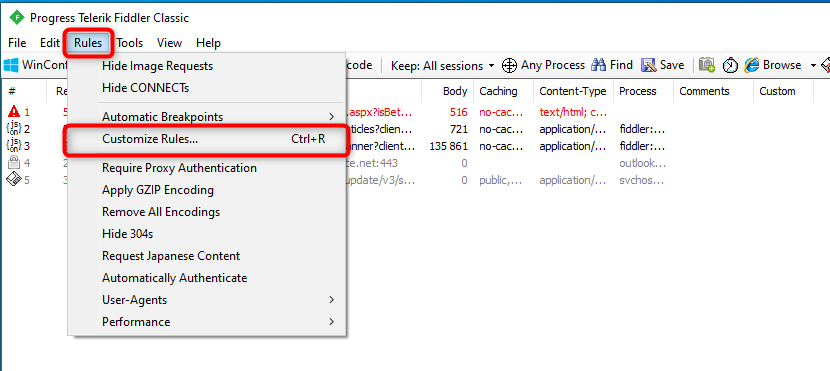
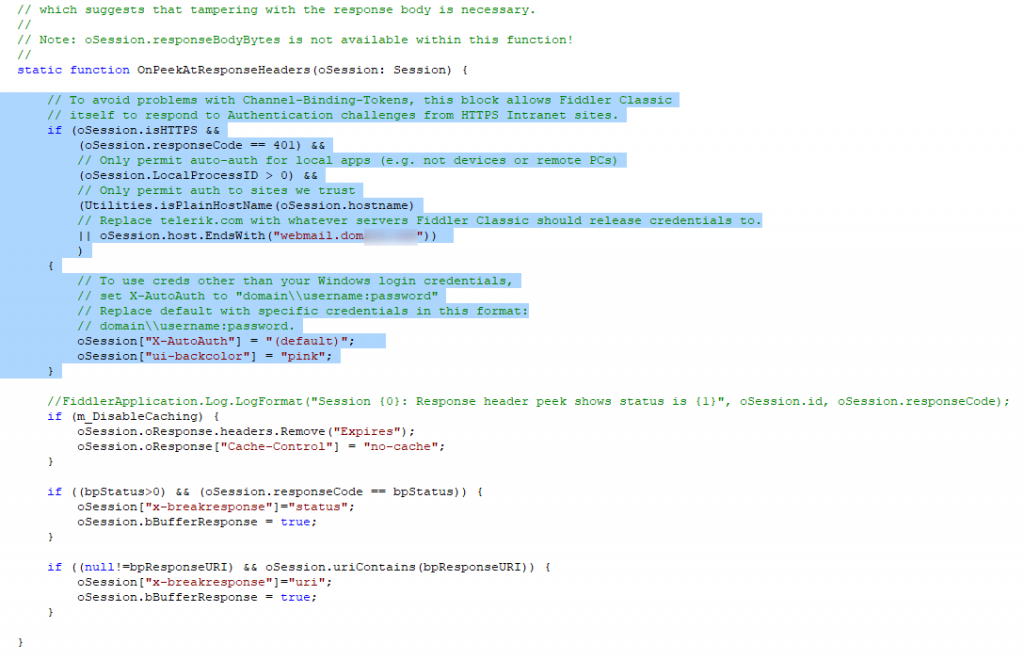
For FIDDLER to allow Exchange connection, FIDDLER itself must handle the authentication sequence (respond to the HTTP 401 packet). This can be done by modifying the FIDDLER function OnPeekAtResponseHeaders. At the beginning of the function, code must be added specifying the hostname of your Exchange platform (the URL of its VIP) and the word ‘default’ so that FIDDLER uses the Windows session to authenticate with EP enabled.
// To avoid problems with Channel-Binding-Tokens, this block allows Fiddler Classic
// itself to respond to Authentication challenges from HTTPS Intranet sites.
if (oSession.isHTTPS &&
(oSession.responseCode == 401) &&
// Only permit auto-auth for local apps (e.g. not devices or remote PCs)
(oSession.LocalProcessID > 0) &&
// Only permit auth to sites we trust
(Utilities.isPlainHostName(oSession.hostname)
// Replace telerik.com with whatever servers Fiddler Classic should release credentials to.
|| oSession.host.EndsWith("Exchange_Url"))
)
{
// To use creds other than your Windows login credentials,
// set X-AutoAuth to "domain\\username:password"
// Replace default with specific credentials in this format:
// domain\\username:password.
oSession["X-AutoAuth"] = "(default)";
oSession["ui-backcolor"] = "pink";
} 
With this configuration Exchange connection is done with FIDDLER open.
Lionel TRAVERSE
Microsoft 365 Certified Administrator Expert
Microsoft Certified Trainer
lionel.traverse@admin365.fr