Introduction
The MS365 cloud has banned “basic” authentication. Only “modern” authentication is available. In this context, an older application that uses SMTP to send mail will be affected. Implementing an SMTP connector dedicated to this application is currently the solution that will enable the application to send legitimate emails without authentication in a secure environment..
Configuring an SMTP connector
In the Exchange administration interface, you need to create an SMTP connector.
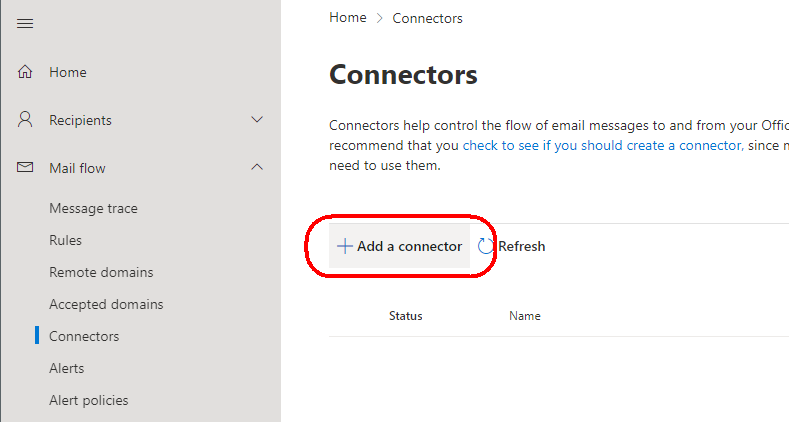
Select the type “Your organization’s mail server”:
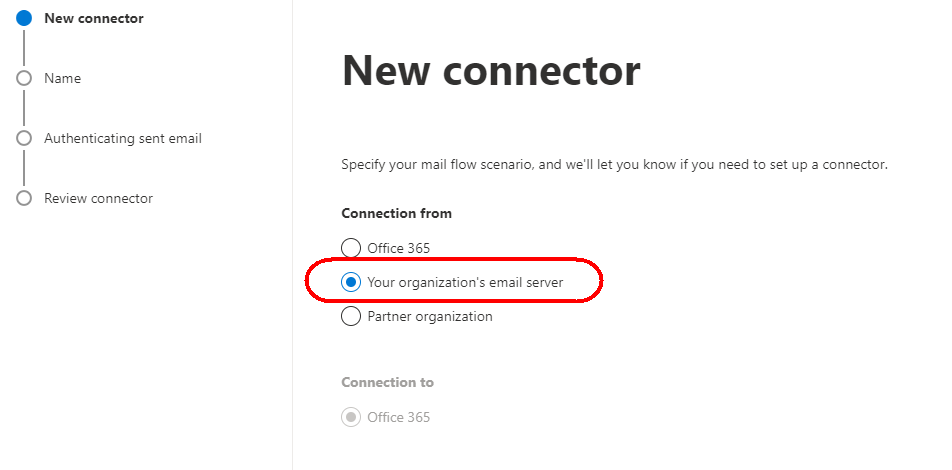
Give your connector a name:
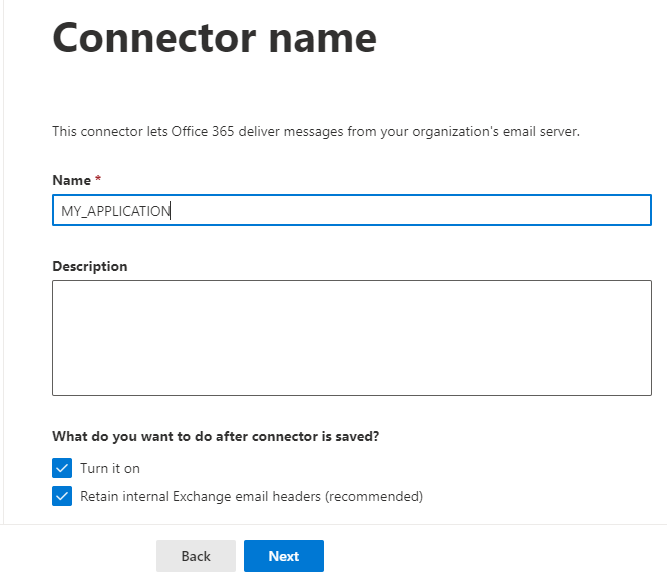
Specify the public IP address of your application and only leave the flow open to MS365 in SMTP for this application:
Validate the creation of your connector:
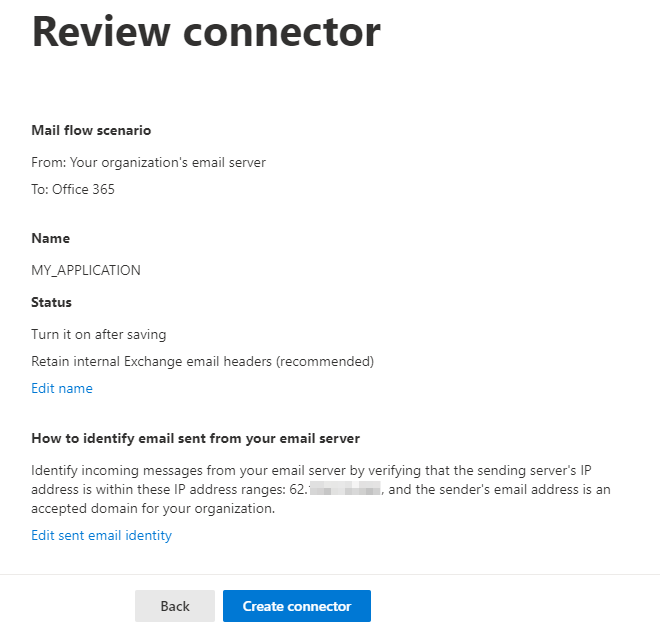
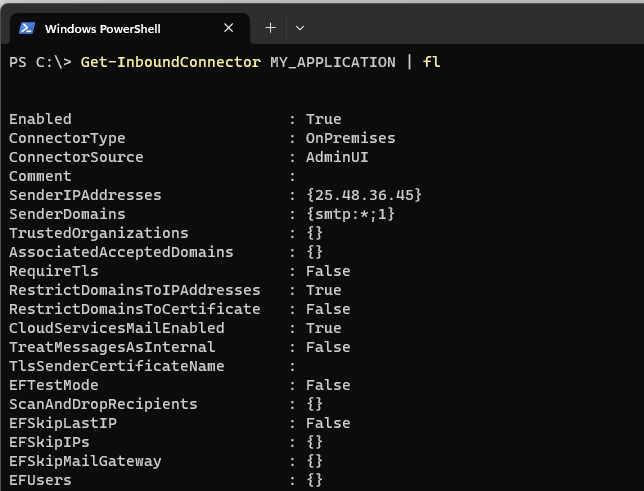
At this stage the application which is behind the IP address will be able to send SMTP mails with any email address of your MS365 tenant. The SMTP server to use without authentication is “_tenant_name_.mail.protection.outlook.com”.
Note: It is recommended to use the email address of a mailbox that has an Exchange Online license in order to benefit from “antivirus services”. Using a shared mailbox without a license can cause problems.
Securing the address used by the application
It is recommended to limit the email address that the application can use to send emails using this connector. To do this, you must configure a transport rule in the Exchange Online administration interface:
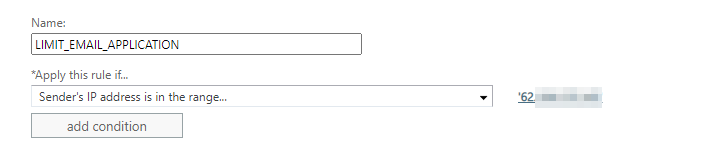
The rule will apply to the IP address of the application:
Any message she tries to send will be delivered to the MS365 quarantine:
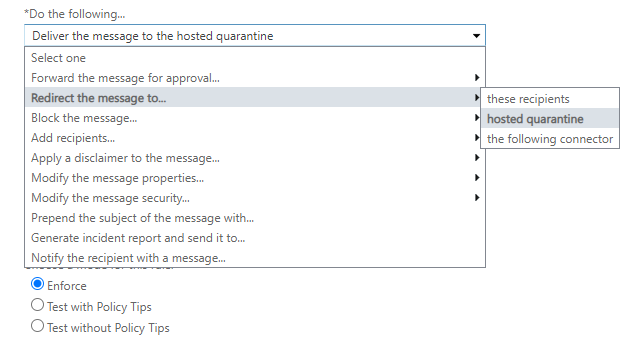
Unless the address used is the address that the application should use:

Once this transport rule is in place, the application will be able to send emails via the SMTP connector but only with the authorized email address. Any other mail will be delivered to the MS365 Defender quarantine (https://security.microsoft.com/quarantine).
Configure Anti-Spoofing for the application
Your application will be able to send emails to yout tenants’s mailboxes and to external email addresses.
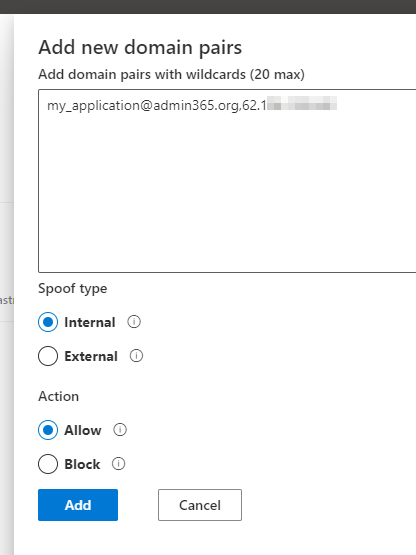
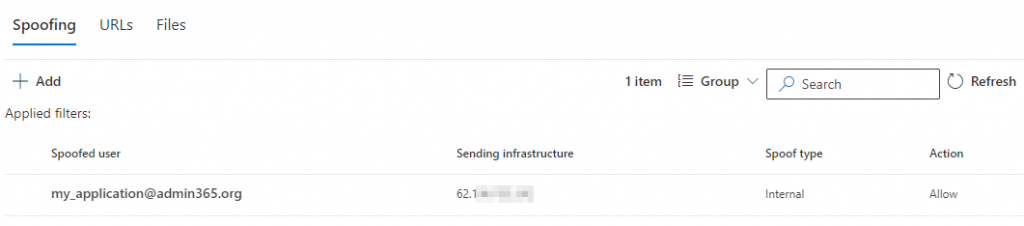
To prevent emails sent to your internal mailboxes from being seen as SPOOFING, you can configure a SPOOFING policy for the IP address of your application via the MS365 Defender administration tool https://security.microsoft.com/tenantAllowBlockList. Authorize the IP address of your application to SPOOFING on the email address it uses:
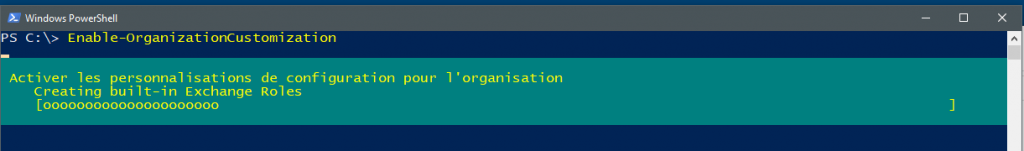
Remark: Before to start, if necessary, you must first authorize the customization of your Exchange Online organization using the Enable-OrganizationCustomization Powershell command:
Lionel TRAVERSE
Microsoft 365 Certified Administrator Expert
Microsoft Certified Trainer
lionel.traverse@admin365.fr