This article explains how to manage or block Direct Send. But what is “Direct Send” ?
Microsoft 365 allows you to receive emails from any email address, including messages sent from addresses within your own tenant. We refer to this type of email as “Direct Send,” and many people may perceive it as a form of spoofing.
The MX servers (Exchange Online Protection) receive these emails without requiring authentication. By default, Exchange Online accepts any email that appears to come from your domain or from an existing mailbox within it. It then delivers the message to the user’s junk email folder. This type of email typically receives a spam score of 5.

If you want to manage or block these Direct Send messages to avoid any confusion for your users, two solutions are now available:
- Add a transport rule in Exchange Online. This method allows you to manage Direct Send granularly with the quarantine usage.
- Use the RejectDirectSend option in Exchange Online to globally block Direct Send.
Use transport rule and quarantine to manage Direct Send
Start to create an Exchange online transport rule.

Specify that the sender is located outside your organization:

Specify that the sender has an email address with one of your different domain names declared in your tenant:

You must choose the actions that apply to this type of email.
A safe option may be not to delete this type of email but to send them to the MS365 quarantine:
- Add a prefix to the message such as [antispoofing]
- Raise the SPAM level from 5 to 7 in order to send the email to the MS365 quarantine and no longer to the user’s mailbox


Overall, the transport rule will include 2 criteria and 2 actions.
You can also add exceptions. For example, if you want that your scanners & printers are able to send emails without authentication (see the related article for more details).

You can also choose to configure this transport rule via powershell commands:

Once this rule is in place, if a “spoofing direct send” email arrives on your MS365 tenant, it will go directly to the MS365 quarantine and you can access it via the security administration tool. The blocked “spoofing” emails will only be accessible inside the quarantine:
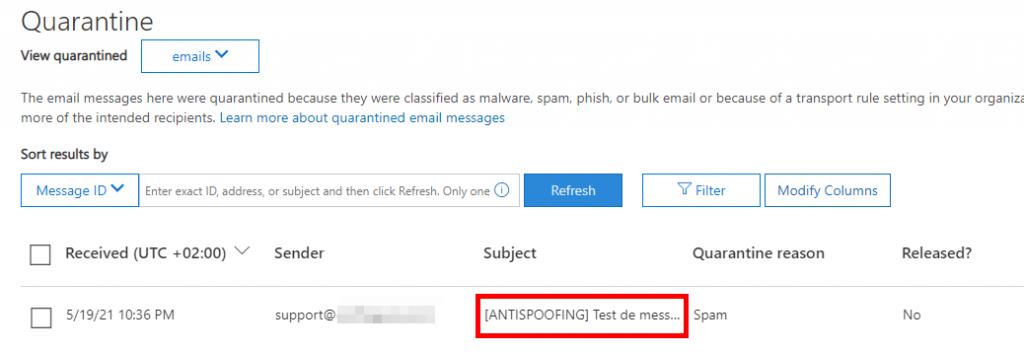
By default, the system keeps these emails in quarantine for 30 days.
You will also be able to list these emails using the powershell command “get-quarantinemessage”:

Block Direct Send with OrganizationConfig parameter
Starting in 2025, Microsoft 365 introduces a new mail flow control parameter called RejectDirectSend. This feature allows administrators to block the reception of emails sent using the “Direct Send” method, which is commonly used by devices or applications that send mail without authentication. You can block Direct Send on the organization level with the Exchange powershell command Set-OrganizationConfig
Set-OrganizationConfig -RejectDirectSend $trueYou can also check the value with a Get-OrganizationConfig command.

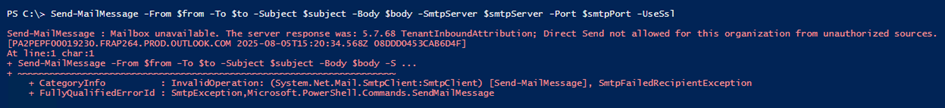
Once Direct Send is blocked at the tenant level, you will see a new error message if you attempt to send emails using Direct Send: 5.7.68 TenantInboundAttribution; Direct Send not allowed for this organization from unauthorized sources.
By Lionel TRAVERSE
Microsoft 365 Certified / MVP Microsoft 365 & Graph